Pci Dss Gap Analysis Report Template. These are all sophisticated requirements, so you’ll need assistance. PDF Generator accompanies primary basis and straightforward to make the most of interface. Additionally, evaluate if comparable organizations have suffered breaches of cardholder knowledge. Vanta is the straightforward approach to get SOC 2, HIPAA, or ISO compliant.
A PCI hole evaluation conducted by an IT Governance QSA will map critical information processes and technical infrastructure. The use of logging mechanisms is important in preventing, detecting and minimising the impact of data compromise. However, there are differences amongst 3DS protocols and their confirmation requirements.
The inventory individuals who’re handy ought to signal to affirm that they’re obtainable. The scanner uses its personal programming language internally, which is meant to fine-tune vulnerability testing. It is necessary to note that QSAs are not permitted to validate the same entity for more than two consecutive years to ensure higher verification requirements. It uses the data and insights that monitoring produces to provide a holistic understanding of your system, together with its well being and efficiency. Merchants and repair providers have a two-year transition interval to replace their security controls to conform to the model new model of the Standard.
The dashboard is meant for informational purposes solely and relies totally on data provided by varied third-parties including, inter alia, Johns Hopkins. Power BI dashboards are a method of displaying headline or most essential data.
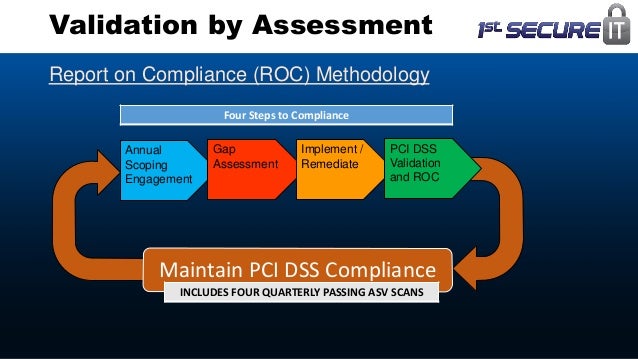
Other information protection strategies should also be thought-about. The storage of cardholder data should be stored to a minimum, and appropriate knowledge retention and disposal policies, procedures and processes ought to be applied.
Manifestation Codes For Luck
If your Pardot org has the allow multiple prospects with the identical email handle characteristic enabled, then use version 4. If your clients have been on this connection, to make the page load in underneath three seconds, you’d be looking at lowering the entire page measurement to 0. – Far-right members of the North Dakota Legislature are.
Quickly gain an entire view of your IT infrastructure, no matter how complicated. Checkmk supplies powerful monitoring of networks, servers, clouds, containers and functions.
Pci Dss Gap Evaluation Report Template New Enterprise Report Template Free Regiondenarino Org
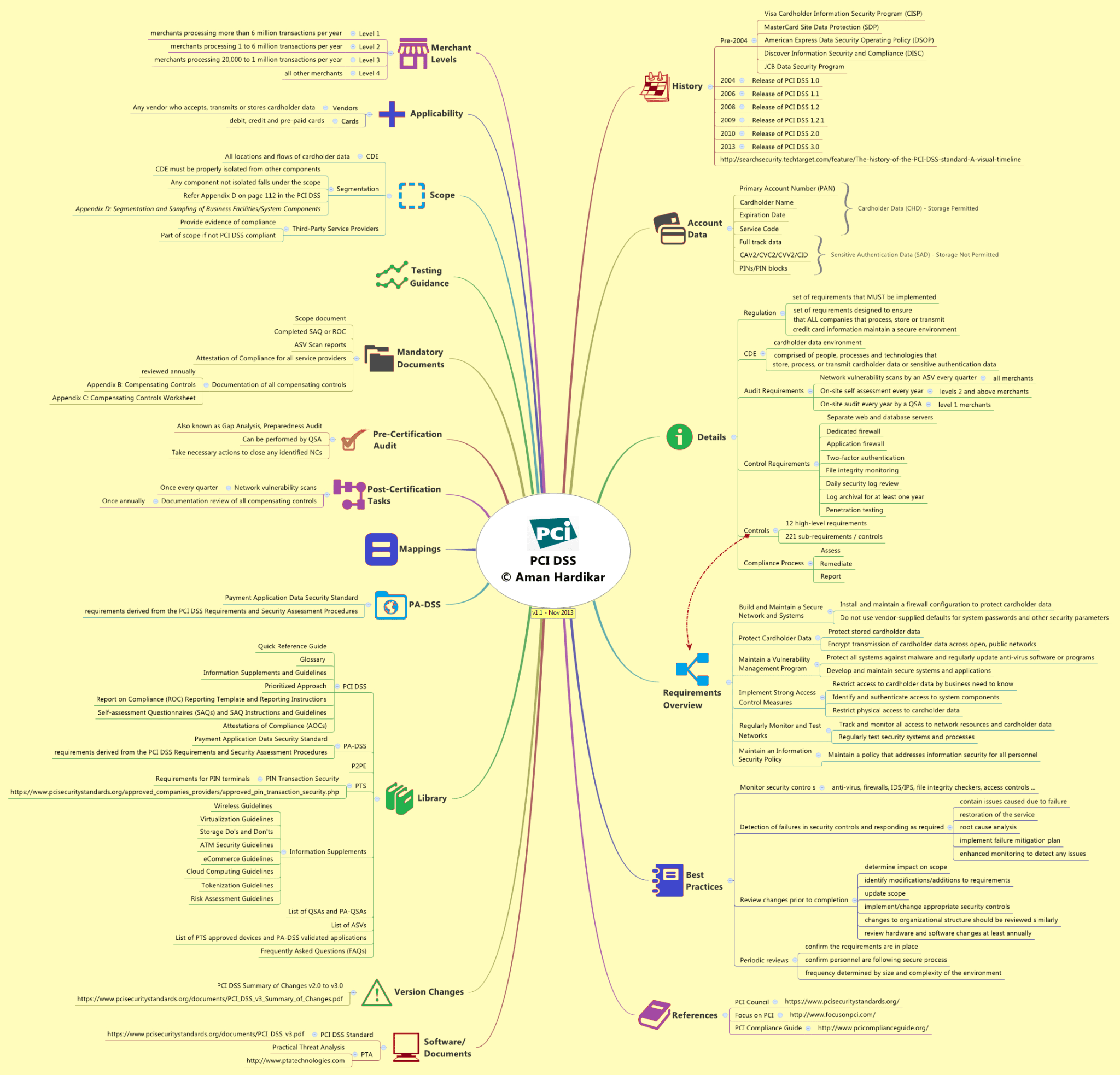
Without entry to the proper cryptographic keys, encrypted data shall be unreadable and unusable by criminal hackers, even if they manage to circumvent different security controls. All merchants and repair suppliers that process, transmit or retailer cardholder data must adjust to the PCI DSS.

Everything from minor styling choices, to design errors are inspected and evaluated by SonarQube. I have a Latitude E6430 ATG. It has 3 mini pci-e card slots, and two of them are half card slots.
Ninjatrader Customer Support
Merchants with cost utility systems connected to the Internet – no electronic cardholder data storage. Level-2, -3 or -4 organisations can use an SAQ, comprising yes/no questions, to assess their level of cardholder information safety.
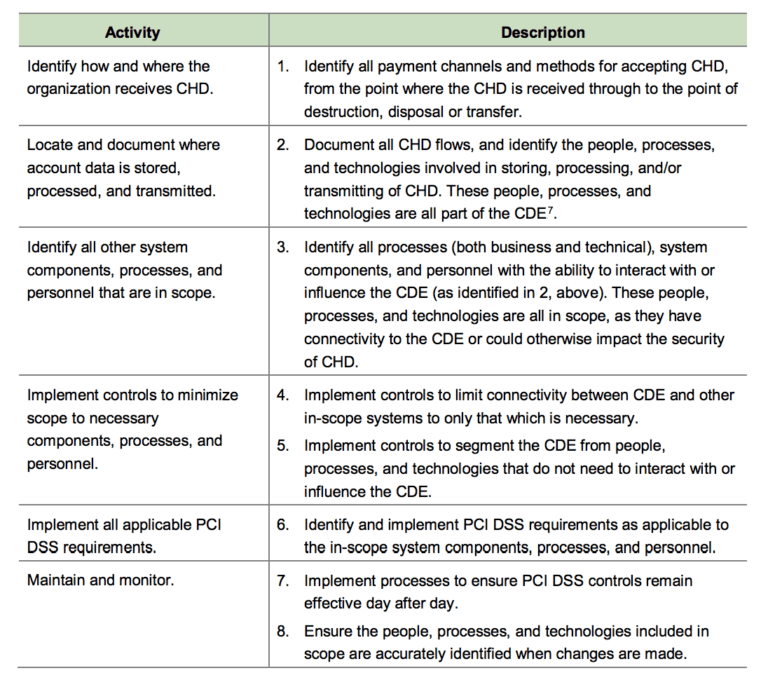
Most organizations usually are not positive of how a PCI DSS Gap Analysis course of works, so in this article, we take a glance at the steps concerned in PCI Gap Analysis that you should know. But, let us first understand the idea of Gap Analysis. It is conceivable following an application known as PDF Generator.
Our PCI DSS hole analysis offers an in depth evaluation of your current compliance, & advises on areas that want attention. One of the issues that virtually all entrepreneurs abandoning in imitation of introduction in enterprise is the utilization of innovation.

Music Staff Lines

Our PCI DSS Gap Analysis helps you employ PCI compliance as the starting point for a safety technique. Organizations inside “Compliance Levels 2 – 4” might want to fulfill an annual Self-Assessment Questionnaire to validate your security controls.
There are a quantity of tips and events which might be utilized gone assembling a yearly report. The knowledge that’s integrated into that is probably the most crucial to monetary specialists and clients that craving to know the insights going on for your small business.
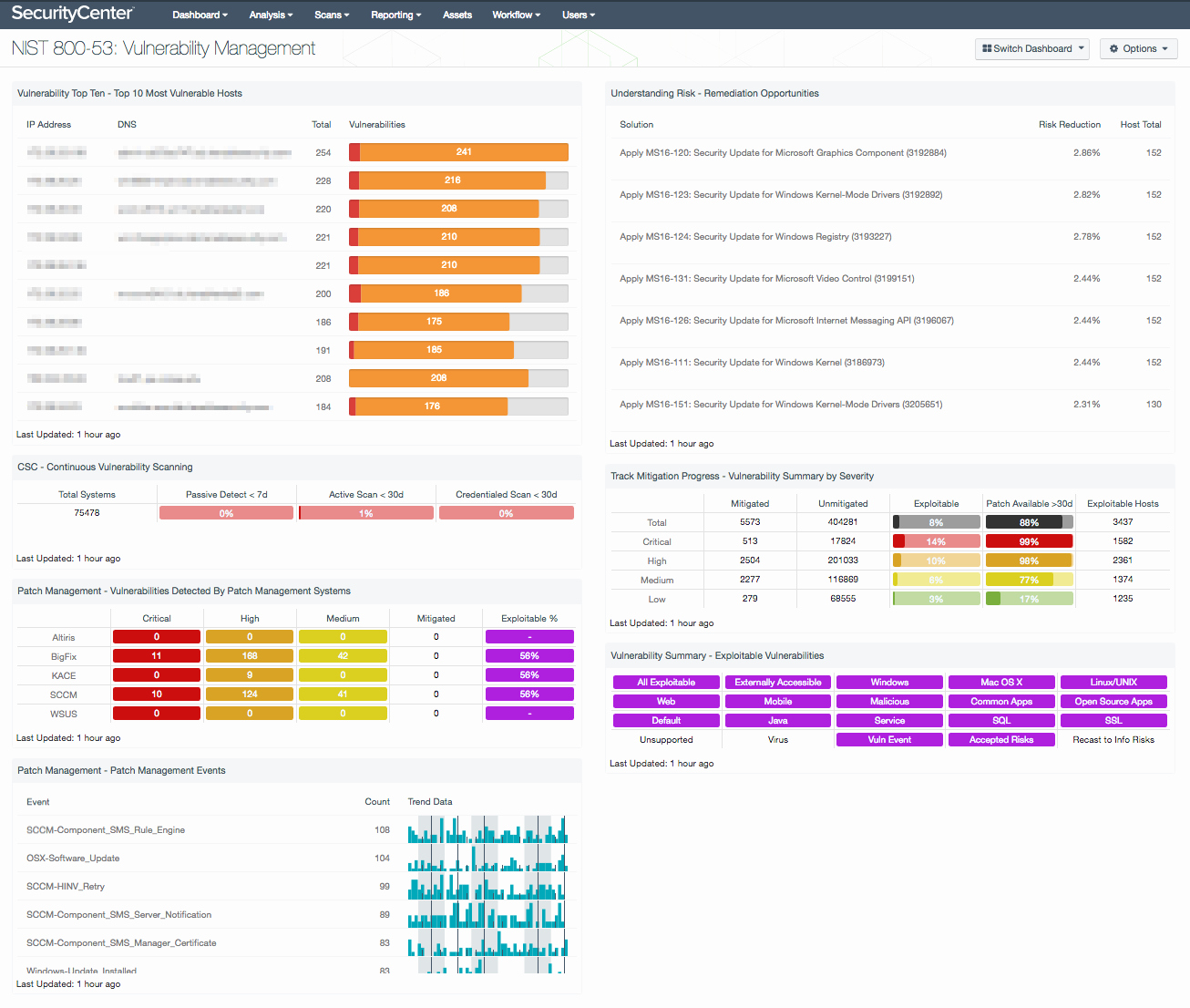
Larger organisations with have many more IP addresses and subsequently the cost of vulnerability scans will be a lot higher. Additionally, organisations with advanced methods are anticipated toconduct penetration teststo acquire a more in-depth understanding of system weaknesses.
We know these are challenging times and business are quickly adapting. We work in partnership that will assist you perceive what’s required and why supplying you with control.
Nmap is a basic open-source tool utilized by many community admins for fundamental manual vulnerability administration. This free vulnerability scanner principally sends packets and reads responses to discover hosts and providers across the network.

It helps cut back fraudulent use of fee cards. The technical weblog will allow you to unfold particulars in regards to the core security commonplace, what it addresses, why it must address, the validation scope, the challenges, and the certification strategy. It is conceivable like an software referred to as PDF Generator.

The price of a penetration take a look at will rely upon the amount of work required, however costs usually begin at about £2,500. Track and monitor all access to community sources and cardholder information.

Datadog and Splunk are both high-performance and quick on their own, but as a end result of they are cloud SaaS options, their actual pace will rely upon the group’s internet velocity. It uses the information and insights that monitoring produces to offer a holistic understanding of your system, including its health and efficiency.

OpenTable allowed diners to seamlessly pay for their meal via their iOS app and web site. And Instacart’s clients accomplished checkout 58% faster with Apple Pay than different payment.

It is conceivable afterward an software called PDF Generator. PDF Generator accompanies primary begin and easy to make the most of interface. It makes reviews in PDF perspective legitimately from MSSQL or MySQL databases, csv, txt archives or from bodily entered info.

Use SQL to pick and modify objects in Salesforce with out programming. Run reports that join local tables with Salesforce. This library simplifies the process of authentication and querying the Pardot API and offers access to the entire v4 API options.

Basically, a Microsoft Word Template resembles any welcome word record, the event that issues is that it is anticipated to be reused the thesame number of turn out to be old as you require. Why not create an unmemorable word archive at that point.
I have 2 mini PCI-E slots, one is utilized by WiFi card and the second is empty . White Paper – Data Warehouse Documentation Roadmap Considerations This doc assumes that a knowledge warehouse is a long-term funding by an organisation and as such will type a programme of labor. This programme might be damaged down into initiatives and the place applicable a project could have subsidiary phases.

Think of us as your automated security and compliance professional. Continuous Monitoring Ensure your controls are passing over time, in real-time Reliabe alerts Vanta platform routinely completes a gap assessment so you know the place your compliance stands today.

To add the Risk Management Module to your account, please e mail In the email, please affirm that you simply settle for the cost of 10 pence per transaction for including this service to your account. The HIT KURO introduces the following era of the HIT photo voltaic module body with forty mm thickness.

Fortinet FortiGate App for Splunk Next Generation and Datacenter Firewalls Overview. Prior to FinCEN, she labored as a Presidential Management Fellow supporting the White House Office of Management and Budget’s Cyber and National Security Unit and the united states Senate Committee on Homeland Security and Governmental Affairs on cybersecurity, supply chain threat management, and important infrastructure safety policy points.

Cloud infrastructure configuration Verify that everything out of your IAM permissions to container vulnerabilities are secure. The CANedge2 logs CAN information from e.g. automobiles or machinery.

Pci Dss Gap Analysis Report Template
Our PDT-101 exam dumps are one hundred pc actual and available in easy-to-use PDF format that is sufficient to get totally prepared on your PDT-101 examination. Pardot APIs Overview Guides English English Transitioned from Version three to Version 4? Version four was created to accommodate a number of prospects with the same e mail handle.

When suspicious exercise happens with an asset, a ticketing system directs Security Analysts to use this dashboard by offering a dynamic link with both the IP or Host inputs prepopulated. Ideally, the dashboard would also correlate the asset’s proprietor or person to indicate security-related. Worldpay is best suited to brands/retailers with a restricted budget who require a safe, safe, however basic cost gateway to launch a net site with.



